Getting Started
MACAT is a simple Adversary Simulation utility designed to be used on typical corporate workstations.
Danger
Read the Terminology section below. Seriously. It will help a lot to know how MACAT refers to its different components.
Who should use MACAT
MACAT is designed to be used by CyberSecurity Professionals. Particular groups that will find the most value are:
- Threat Hunters
- Detection Engineers
- Cyber-Threat Intelligence Analysts
- SOC Team Members
- Purple Team Operators
- Cyber Defense Tool Implementation Specialists
- Blue Team Defenders
- General CyberSecurity Analysts
Why you should use MACAT
MACAT is designed to be a simple, easy to use, and effective tool for simulating adversary behavior on a corporate network. It is designed to be used by CyberSecurity Professionals to test telemetry gathering, detection capabilities, validate security controls, and improve overall security posture.
MACAT has a low learning curve and time-saving features making it the fastest way to get started.
Terminology
Technique
A Technique refers to a MITRE ATT&CK Technique which is a way of categorizing the type of attack an Adversary might use against a target. MACAT uses Techniques as way of describing and organizing procedures.
MITRE ATT&CK visualizations often show a heatmap which looks like a table with the techniques shaded in different colors. This can be a useful visualization for visualizing where you’re focusing on building defenses or describing the areas where a threat actor focuses their attacks, but from a defender perspective, be aware that there can be many procedures categorized by each Technique. Additionally, individual procedures might require different defenses even if they’re categorized by the same Technique.
You may run across the phrase “MITRE ATT&CK is not a bingo card” and this means that you often should not consider an entire Technique ‘defended’. The concept of “MITRE ATT&CK coverage” should be considered an aspirational goal and not something you will achieve by creating targeted defenses against one or a handful of procedures for a Technique. MACAT and the Atomic Red Team project do not contain an exhaustive list of procedures for a technique.
Procedure
A Procedure is a specific implementation of a technique including the concrete steps or commands that an adversary would execute on a target system or asset.
The Atomic Red Team atomic tests are all procedures. Example Procedure - Scheduled Task Creation
MACAT can assist you in organizing, executing, and creating Procedures.
Simulation
A Simulation in MACAT is a collection of procedures that are executed together to simulate adversary behavior.
Simulations can represent any kind of grouping of different procedures: a single-stage attack scenario (like privilege escalation), a multi-stage campaign simulating the actions of a specific Threat Actor, a set of related procedures grouped for a specific purpose (example: testing telemetry coverage for Initial Access), or an unrelated group of prioritized procedures you’re interested in testing. Simulations are user-created and customizable, allowing defenders to test their environment against a wide variety of realistic behaviors.
TTP
TTP stands for Tactics, Techniques, and Procedures which is common language for describing how adversaries operate. I don’t recommend using this vocabulary, but you may run across it in other publications. It’s vague and referring to procedures as ‘TTPs’ confuses the intention of adversary simulation exercises.
- Tactic: The goal or objective of an attacker (Persistence, Credential Access).
- Technique: A general method to achieve a tactic (Create Account).
- Procedure: A concrete implementation of a technique (using
net userto create a local admin account).
MACAT primarily focuses on Techniques and Procedures but makes it easy to align them with the larger TTP structure for planning and reporting.
Threat Profile
A Threat Profile is reference to an adversary group, malware family, or threat scenario. In MACAT, this specifically refers to MITRE Enterprise ATT&CK Groups and uses the STIX identity object as a unique reference.
Recording procedure-level information about adversary Threat Profiles helps users categorize and document procedures for targeted simulation or research.
Procedure Tag
A Procedure Tag is a keyword or label applied to a procedure to help with categorization, filtering, and organization.
Some examples of useful tags are:
- Common adversary use scenario (
ransomware,infostealer,rootkit) - Organizational target (
government,financial-services) - Defense priority (
critical,priority-0)
Users can use tags to quickly group procedures during simulation creation or to identify gaps in coverage.
- Common adversary use scenario (
Defense Tool Type
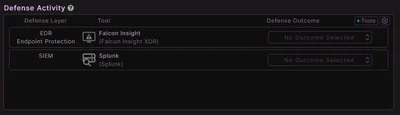
A Defense Tool Type is a classification used in MACAT to associate a procedure with types of detection or prevention tools that may observe or block its activity.
Examples include:
- edr (Endpoint Detection & Response)
- siem (Security Information and Event Management)
- firewall
- application-whitelisting
- dlp (Data Loss Prevention)
This helps users understand which tools may generate alerts or logs when a procedure is executed, and where to focus when validating detection rules or telemetry pipelines.
If integrating with VECTR, this information is used to inform VECTR which defense tool types should be used in recording the defense result of a procedure/test case.